Weekly devlog at worm-blossom.org.

Weekly devlog at worm-blossom.org.
A prefix authentication scheme that is more efficient than the one used in certificate transparency. Supersedes Bamboo.

A macro system for generating plaintext files. Suitable for producing web-native scientific papers such as this one. And the website you are currently reading, of course.
A Rust library of abstractions for lazily producing or consuming sequences.
A tool for scheduling meetings across timezones, mapping UTC offsets to emoji. Carrying on some of @cinnamon’s light.
A family of randomized set data structures that generalizes the zip-trees to work more efficiently in the presence of cache hierarchies. G-trees have applications for set fingerprinting and membership proofs.
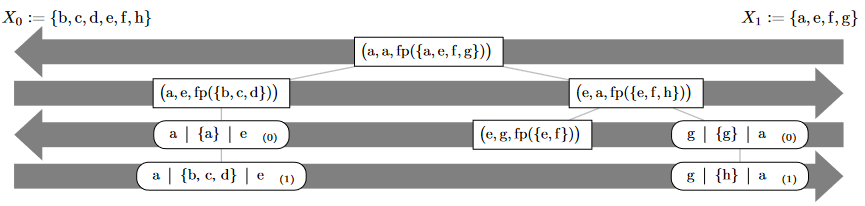
Range-based set reconciliation is a simple approach to efficiently computing the union of two sets over a network, based on recursively partitioning the sets and comparing fingerprints of the partitions to probabilistically detect whether a partition requires further work.
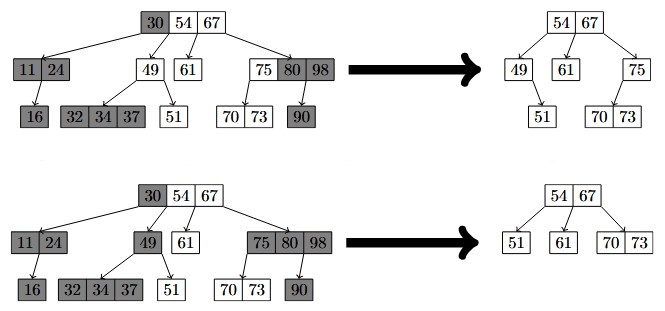
Range-based set reconciliation used to require non-standard hash functions with certain homomorphic properties. This paper describes how to do away with these and use regular Merkle trees instead.
Like certificate transparency logs, but more simple and more efficient.
Musings on how a bulk transclusion operator in a hypertext system can subsume common UI patterns that traditionally require ad-hoc logic to implement.
Sam and I released ufotofu, a Rust library for working with streams and sinks. The website is... something.
Weekly updates from worm-blossom, the moniker under which Sam Gwilym and I do (primarily) computer things.
The Willow project got funding for implementing a new hash function. Here I explain the gist of it.
An entirely serious alternative to the semantic versioning specification.
An essay on how to achieve mutable hypertext without automatically suffering from link rot, and why this matters.
A few of my favourite Beatles songs.
How past me approached coding.
A collection of treasures — works that have been important to me.
A small puzzling game I once wrote while being sick.